Best practices: Protecting from phishing attacks
A phishing attack happens when someone attempts to trick you into sharing personal data online. For example, a scammer might send you an email that looks like it’s from your service provider so that you’ll send them sensitive information about your account such as passwords or credit card information.
Anyone can become the target of a scammer. Often scammers send phony emails or direct messages on social networks that ask you to visit a link, download a file or open an attachment. These messages are often created to look like they came from legitimate sources. If you take any of these actions, your device may be infected with malicious software that will allow the attackers to steal your personal data such as login credentials and banking or credit card details.
You can protect yourself against phishing by carefully reading every message that hits your inbox. If you see any signs of phishing, refrain from taking any of the requested actions (sending account information, clicking links, etc.) The first step you can take right now to prevent phishing is to use a different email address for your public contact info than the one you use for your store account login.
Detect signs of phishing
If you receive a message that asks you to provide or update your personal data, like login or bank credentials, refrain from taking any actions if you see any of the following warning signs:
- The message contains mismatched URLs. The URL shown in the email and the URL that displays when you hover over the link are different from one another.

- It begins with a vague greeting like “Dear account holder.” Reputable companies will have your name in the salutation, as opposed to “valued customer” or “to whom it may concern.”

- It is poorly written and contains typos, misspellings, unnecessary capitalizations, etc. Legitimate messages usually do not have major spelling mistakes or poor grammar.

- It sounds urgent or threatening. Invoking a sense of urgency or fear is a common phishing tactic. Beware of messages trying to scare you into acting without thinking.
- It contains attachments from unknown sources that you were not expecting. Inclusion of malicious attachments with malware is a common phishing tactic.
Keep your firewall and security software up to date
Make sure that your firewall and antivirus software are updated regularly and working properly. Although it can’t guarantee complete protection, updated security software and firewall protection is the first line of defense.
Make sure your connection to a website is secure
When you open a website where you may be asked to provide a username and password or any other sensitive information, make sure that the website is using a secure HTTPS connection.

Be extremely careful when clicking links you receive via email
Before you click on a link inside an email, you must be absolutely certain who the email is coming from and that the link is secure. If you want to test the link, you can open a new browser window in incognito mode and type in the URL instead of clicking the suspicious link.
Beware of email attachments
Do not open any attachments, unless you are expecting them and know what they contain. These attachments could infect your system with viruses and malware that could damage the files on your computer, steal your passwords or spy on you without your knowledge.
Don’t post your store account email in public places
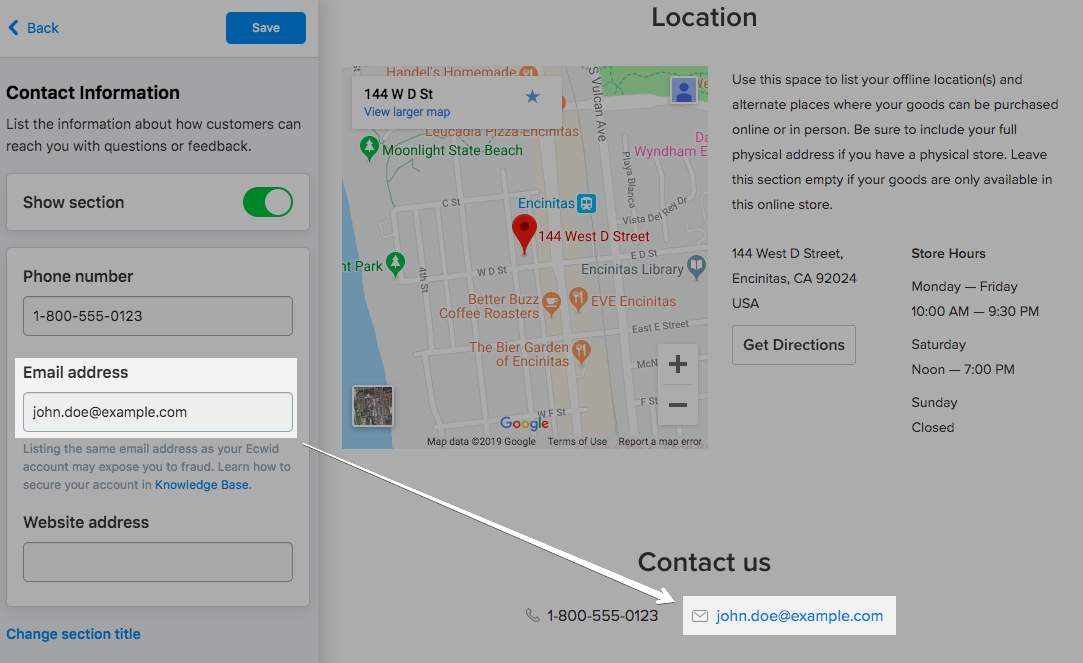
Do not publicly post the email address that is linked to your online store account, as it may expose you to phishing attempts by online scammers. Always use a different email address for public spaces such as the contact email address on your website.
If you are using Instant Site, make sure to include your public email address instead of your store account email address. You can change your contact email in the store admin panel → Website → Edit Instant Site design and content → Contact Information.
Clear up your concerns using alternative methods of communication
You can resolve any concerns about a suspicious message by talking directly to someone at the organization that supposedly sent the email. When you call the company or organization, use a phone number that you already have on file or one that appears on multiple reputable online sources. Do not use the contact details listed in the email. The company or organization should be able to confirm over the phone if the suspicious email is legitimate and from them.